Table of Contents
Also Read: Comprehensive Guide to Network Security: Protecting Digital Assets
Introduction

In today’s interconnected world, information security has become more critical than ever. The explosion of digital data and reliance on technology expose individuals, organizations, and governments to cyber threats. As the global economy becomes increasingly reliant on digital ecosystems, the vulnerability of sensitive information grows proportionately. This evolving dynamic underscores the necessity of not only understanding information security but also implementing comprehensive and proactive measures to counter these threats. Ensuring robust security frameworks is no longer optional—it is integral to the functionality and reputation of modern enterprises.
Understanding Information Security
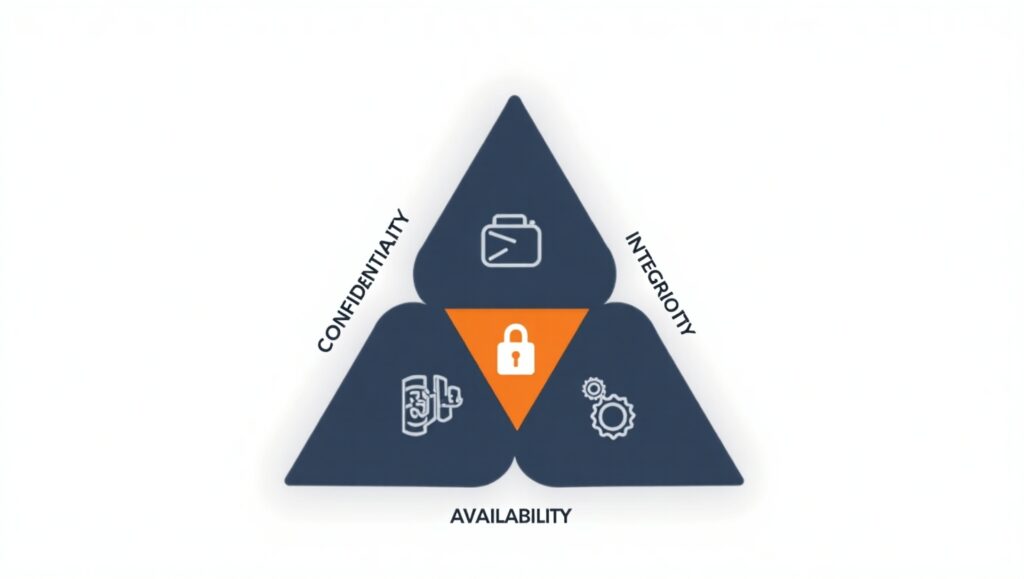
Information security (InfoSec) involves practices and processes aimed at safeguarding data in both digital and physical forms. The overarching objective is to ensure the preservation of what is referred to as the CIA triad:
- Confidentiality: Ensuring sensitive information is accessible only to authorized individuals. Mechanisms such as encryption, multifactor authentication, and strict access protocols are vital.
- Integrity: Protecting data from unauthorized modifications to maintain its accuracy and reliability. Validation procedures and checksums often supplement database management systems to support this.
- Availability: Ensuring that information is available to authorized users when needed. This principle underpins strategies like disaster recovery planning and system redundancy to counter unexpected downtimes.
By upholding these principles, organizations are better equipped to counteract the spectrum of evolving threats targeting critical data repositories.
Types of Information Security
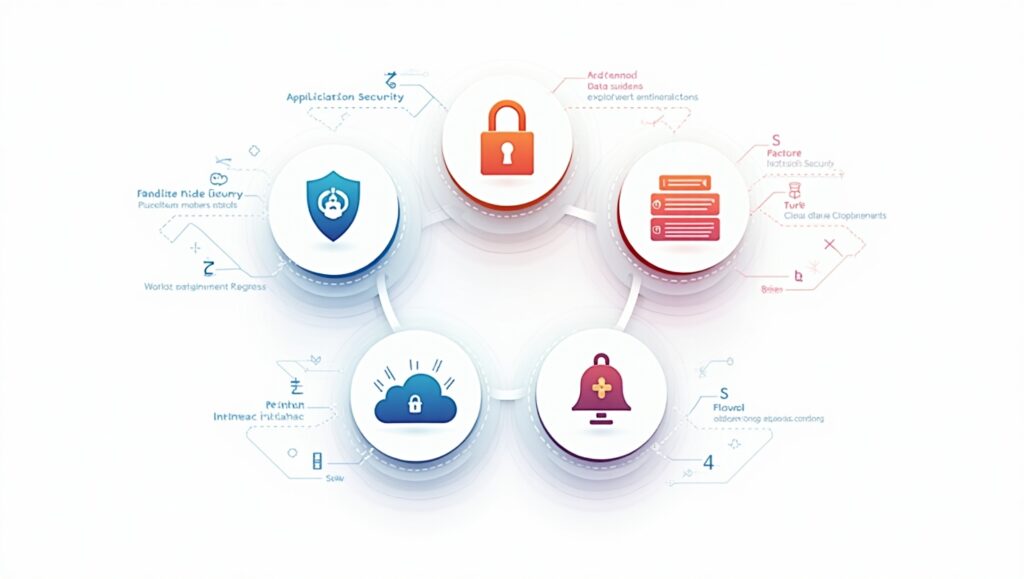
Application Security
Application security focuses on securing software from vulnerabilities that attackers can exploit. This domain addresses risks originating from coding flaws, architecture misconfigurations, and inadequate encryption methods. Measures include:
- Secure coding practices adhering to established frameworks like OWASP.
- Periodic vulnerability assessments and penetration testing tailored to application lifecycles.
- Real-time monitoring of API interactions, complemented by input validation processes.
Data Security
Data security encompasses methods of protecting information across its lifecycle—from its generation through storage, usage, transmission, and eventual deletion. Specific interventions include:
- Encryption: A cornerstone practice ensuring that data—in transit or at rest—is converted into unreadable formats, accessible only via decryption keys.
- Access Controls: Structured access management systems utilize identity authentication, bolstered by tools such as Role-Based Access Control (RBAC).
Network Security
The increasing integration of hybrid infrastructures necessitates network security paradigms that adapt to both on-premises systems and the cloud. Critical techniques include:
- Designing multi-layered firewall configurations complemented by intrusion detection systems.
- Deploying secure Virtual Private Networks (VPNs) to safeguard remote access points.
- Employing network segmentation to isolate sensitive nodes from general traffic flow.
Cloud Security
The widespread adoption of cloud infrastructures introduces unique challenges regarding data sovereignty, elasticity, and third-party dependencies. Effective approaches involve:
- Conducting due diligence assessments of cloud providers to verify compliance with frameworks like ISO 27001.
- Ensuring encrypted connections and data-at-rest policies, often supported by Hardware Security Modules (HSM).
- Adopting containerized security practices within serverless deployments.
Incident Response
Incident response entails systematic detection, investigation, and remediation processes following suspected breaches. Establishing the following is critical:
- A formal incident response plan that delegates specific team member responsibilities during crises.
- Integration of Security Information and Event Management (SIEM) tools for holistic visibility across digital infrastructures.
- Continuous improvements following post-incident reviews to identify systemic weaknesses.
Best Practices for Strengthening Information Security
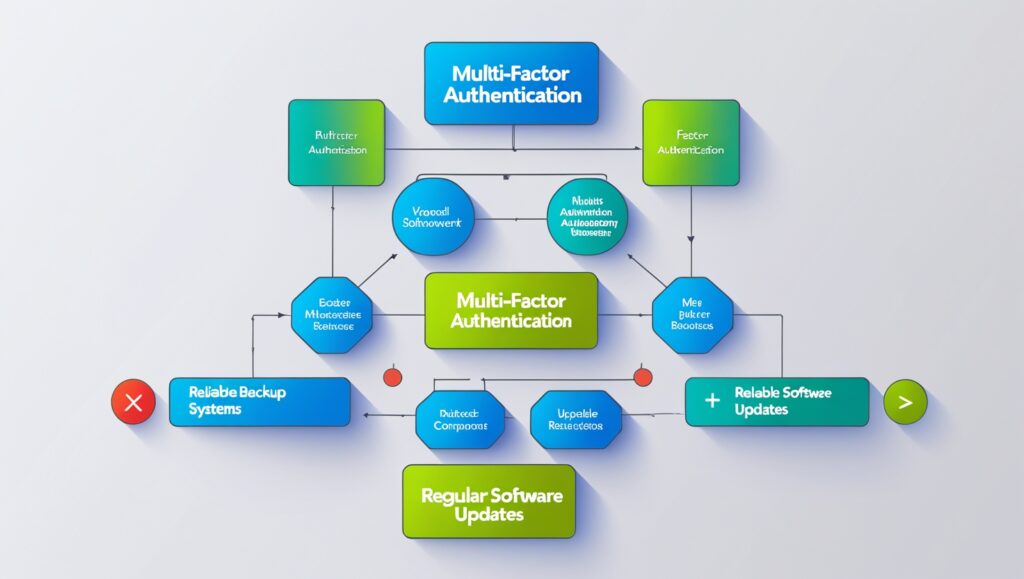
- Regular Updates and Patch Management
- Vigilantly applying patches ensures that security vulnerabilities are resolved before exploitation by malicious actors.
- Educate Employees
- Implement an ongoing cybersecurity awareness program addressing phishing, social engineering, and ransomware tactics.
- Implement Multi-Factor Authentication (MFA)
- Enhance security robustness through dual-layer verification mechanisms beyond traditional password use.
- Backup and Disaster Recovery
- Design layered backup systems comprising local, cloud, and immutable backups. Evaluate and update recovery objectives periodically.
- Conduct Vulnerability Assessments
- Evaluate networked assets, systems, and devices through frequent vulnerability scans. Allocate findings into prioritized risk assessments.
- Governance Policies
- Formalized data governance ensures alignment of security strategies with organizational objectives, incorporating oversight committees or external consultancies as necessary.
The Role of Compliance in Information Security

Adherence to standards like GDPR and HIPAA provides a structured framework for achieving accountability, with mandates focused on risk management, user rights, and transparency. Beyond minimizing the risks of punitive penalties, compliance initiatives:
- Improve internal audit processes while creating demonstrable trustworthiness.
- Reinforce partnerships by guaranteeing reliable data handling practices.
- Serve as foundations for certifications, offering competitive differentiation in the marketplace.
Emerging Trends in Information Security
- Artificial Intelligence (AI): AI-powered systems improve threat detection and enable predictive analysis by identifying patterns indicative of malicious behaviors or anomalies. Machine learning models further bolster adaptive responses to zero-day exploits.
- Zero Trust Architecture: Emerging frameworks like Zero Trust reimagine security boundaries, promoting verification models built on minimal trust. Implementation often merges principles of just-in-time privilege management and encrypted communication.
- Quantum Cryptography: As quantum computing emerges, its implications for breaking traditional encryption present severe challenges. Quantum-resistant algorithms or encryption harnessing entangled photon communication exemplify promising countermeasures.
FAQs
Why is information security important?
Information security is vital for safeguarding both personal and institutional data from potential breaches, ensuring operational resilience and trust-building within stakeholder ecosystems.
What is the CIA triad?
The CIA triad—Confidentiality, Integrity, and Availability—represents the core principles driving effective data protection strategies.
How can individuals protect their personal information?
Leverage unique passwords managed via digital vaults, implement MFA tools, and adhere to minimal data-sharing practices to shield oneself against cyber threats.
What is the role of encryption in information security?
Encryption secures the digital communications pipeline, leveraging algorithms that obfuscate data transmissions or repositories. Only entities possessing decryption keys gain authorized access.
What is a phishing attack?
Phishing deceives individuals into surrendering sensitive credentials, often through fraudulent emails, calls, or websites masquerading as trusted entities.
Conclusion
The growing reliance on technology reaffirms the urgency of prioritizing information security in all sectors. To ensure digital sovereignty and trust, adopting the above-discussed practices strengthens not only infrastructure defense systems but also institutional resilience amid ever-present challenges. Sustained vigilance and proactive adoption of innovative technologies will serve as cornerstones for safeguarding the integrity, confidentiality, and availability of critical data assets.





[…] Also Read: Information Security: Protecting Your Data in a Digital World […]
Оборудование для конференц зала: решение для успешных встреч и переговоров
оснащение конференц залов оборудованием [url=http://oborudovaniye-konferents-zala1.ru/]http://oborudovaniye-konferents-zala1.ru/[/url] .
Take charge of your personal brand with [url=https://createsignature.ru/]create your own signature[/url]. This service makes it effortless to craft something truly unique.
http://blockingbirds.com/bbs/board.php?bo_table=inquiry&wr_id=158670 create initials sig https://www.memoriesandmilestones.net/show_big_cart.asp?Return_To=https%3A%2F%2Fwww%2Ememoriesandmilestones%2Enet%2Fitems%2Fwooden%2Dserving%2Dboards%2Fsushi%2Dclassic%2Dsushi%2Dclassic%2Ddetail%2Ehtm%237323220 create signature 58da691
Оборудование для актового зала: проекторы, световые системы, звуковое сопровождение
оборудование для актового зала школы купить [url=oborudovaniye-aktovyh-zalov1.ru]oborudovaniye-aktovyh-zalov1.ru[/url] .
Оснащение мультимедийным оборудованием: проектирование и монтаж под ключ
оснащение мультимедийным оборудованием [url=https://osnashcheniye-multimediynym-oborudovaniyem1.ru]https://osnashcheniye-multimediynym-oborudovaniyem1.ru[/url] .
Экраны для проекторов: профессиональное оборудование для вашего удобства
экран проекционный купить [url=http://www.proekcionnye-ehkrany1.ru/]http://www.proekcionnye-ehkrany1.ru/[/url] .
Современные технологии для оборудования переговорных комнат
оснащение переговорной [url=https://www.oborudovaniye-peregovornykh-komnat1.ru]https://www.oborudovaniye-peregovornykh-komnat1.ru[/url] .
Получите коммерческий автотранспорт в лизинг на самых выгодных условиях
спецтехника в лизинг [url=http://www.lizing-avto1.ru/specztehnika/]http://www.lizing-avto1.ru/specztehnika/[/url] .
Современное оснащение конференц залов: технология, комфорт, надежность
конференц залы оборудование [url=https://www.osnascheniye-konferents-zalov1.ru/]https://www.osnascheniye-konferents-zalov1.ru/[/url] .
Воплотите мечту о деревянном доме под ключ вместе с нами
строительство деревянного дома под ключ цена [url=http://www.derevyannye-doma-pod-klyuch1.ru/]http://www.derevyannye-doma-pod-klyuch1.ru/[/url] .
Lotnisko Chopina parking – wygodny start i gwarancja miejsca na twoj samochod
parking w Warszawie blisko lotniska [url=https://parking-chopin-48.pl/]https://parking-chopin-48.pl/[/url] .
Установка и ремонт сантехники – лучшие мастера для вашего комфорта
вызвать сантехника [url=1remont-santehniki.ru]1remont-santehniki.ru[/url] .
Scriptie laten schrijven voor een zorgeloze afstudeerperiode
scriptie ghostwriter [url=https://www.scriptielaten-schrijven.nl/]https://www.scriptielaten-schrijven.nl/[/url] .
Тепло и уют в каждом уголке: строим каркасные дома для комфортной жизни
каркасные дома спб под ключ [url=https://www.karkasnye-doma-pod-kluch0.ru/]https://www.karkasnye-doma-pod-kluch0.ru/[/url] .
Discover the secrets to maximizing revenue from affiliate partnerships
partners gambling [url=https://www.affbetx.com]https://www.affbetx.com[/url] .
Автосалоны Новосибирска: покупайте машину легко и безопасно
бу авто в россии купить [url=https://auto-nsksity.ru/]https://auto-nsksity.ru/[/url] .
Лучшие авторазборки в Москве: адреса, цены и отзывы
авторазбор иномарок [url=http://www.avtorzborka-moskva-1.ru]http://www.avtorzborka-moskva-1.ru[/url] .
Построим каркасный дом с индивидуальным подходом к каждому клиенту
каркасные дома спб [url=http://www.karkasnye-doma-pod-kluch1.ru]http://www.karkasnye-doma-pod-kluch1.ru[/url] .
Каркасный дом под ключ: готовые проекты или индивидуальное решение
каркасный дом под ключ спб [url=spb-karkasnye-doma-pod-kluch1.ru]spb-karkasnye-doma-pod-kluch1.ru[/url] .
Экологичные каркасные дома в Петербурге: комфорт и безопасность для вашей семьи
каркасный дом [url=http://spb-karkasnye-doma-pod-kluch0.ru/]http://spb-karkasnye-doma-pod-kluch0.ru/[/url] .
Гран Канария: перфектната почивка за всяко време на годината
гран канария стадион [url=https://www.gran-kanaria.com]https://www.gran-kanaria.com[/url] .
Квалифицированная помощь в психиатрической клинике Петербурга: от консультации до реабилитации
психиатрическая клиника в спб [url=https://www.psihiatricheskaya-klinika-spb-1.ru]https://www.psihiatricheskaya-klinika-spb-1.ru[/url] .
Закажите алкоголь ночью: мы доставим быстро и безопасно
доставка алкоголя на дом [url=dostavka-alcogolya-nochyu-shop.ru]dostavka-alcogolya-nochyu-shop.ru[/url] .
Центр психиатрической помощи Петербурга: мы заботимся о каждом пациенте
платная психиатрическая помощь в санкт петербурге [url=http://psihiatricheskaya-klinika-spb-0.ru/]http://psihiatricheskaya-klinika-spb-0.ru/[/url] .
Контрактные двигатели для Toyota, Honda, BMW и других популярных марок
контрактные двигателя [url=https://www.kontraktnye-dvigateli-moskva-1.ru/]https://www.kontraktnye-dvigateli-moskva-1.ru/[/url] .
Доступные цены на фронтальные погрузчики для вашего бизнеса
погрузчик фронтальный купить цена [url=https://www.xn—-7sbkqfclcqchgmgkx0ae6eudta.xn--p1ai/]https://www.xn—-7sbkqfclcqchgmgkx0ae6eudta.xn--p1ai/[/url] .
Найдите качественные бу запчасти для автомобиля всего за пару минут
купить б у запчасти [url=zapchasti-bu-moskva-1.ru]zapchasti-bu-moskva-1.ru[/url] .
Услуги сантехника: ремонт, монтаж и модернизация водопроводных систем
услуги сантехника в спб [url=https://sanmontazh1.ru]https://sanmontazh1.ru[/url] .
Платная наркологическая клиника: шаг к здоровой жизни без зависимости
наркологическая клиника [url=http://platnaya-narkologicheskaya-klinika.ru]http://platnaya-narkologicheskaya-klinika.ru[/url] .
Казино и ставки на Mostbet: ваш путь к большому выигрышу
mostbet uz yuklab olish скачать [url=https://www.mostbet-uz-bet.top/]https://www.mostbet-uz-bet.top/[/url] .
Круглосуточная доставка алкоголя: качественный выбор напитков для любого мероприятия
доставка алкоголя на дом москва [url=http://dostavka-alcogolya-nochyu-world.ru/]http://dostavka-alcogolya-nochyu-world.ru/[/url] .
Круглосуточная доставка алкоголя на дом: ваш комфортный выбор
заказать алкоголь с доставкой москва [url=http://www.dostavka-alcogolya-nochyu-club.ru]http://www.dostavka-alcogolya-nochyu-club.ru[/url] .
Услуги сантехника для новостроек: монтаж сантехники с нуля
сантехник на дом спб недорого [url=https://www.remontson1.ru/]https://www.remontson1.ru/[/url] .
Установка бойлеров, унитазов, раковин и устранение протечек за один визит
услуги сантехника [url=san-mon.ru]san-mon.ru[/url] .
Юридические аспекты суррогатного материнства: что нужно знать до начала программы
суррогатное материнство [url=mammalogy.su]mammalogy.su[/url] .
Антимонопольный юрист для предотвращения штрафов и решения спорных вопросов
юрист фас [url=https://antimonopolnii-yurist.ru]https://antimonopolnii-yurist.ru[/url] .
Design stamps with handwritten fonts – stamp maker online makes it easy
online stamp design maker [url=https://www.make-stamp-online0.com]https://www.make-stamp-online0.com[/url] .
Лучшие районы для бронирования: где снять квартиру на сутки в Гродно
квартиры на сутки Гродно недорого [url=http://www.newgrodno.ru]http://www.newgrodno.ru[/url] .
Анонимная госпитализация в наркологическую клинику: срочная помощь
наркологическая клиника телефон [url=https://www.platnaya-narkologicheskaya-klinika1.ru/]https://www.platnaya-narkologicheskaya-klinika1.ru/[/url] .
Купить кабины для спецтехники с официальной гарантией — скидки на опт
кабина для спецтехники купить [url=http://www.xn—–6kceqhatfamjizg3a7au2dr1h5d.xn--p1ai/]http://www.xn—–6kceqhatfamjizg3a7au2dr1h5d.xn--p1ai/[/url] .
Free stamp creator online: drag-and-drop interface for effortless designing
stamp maker online [url=http://www.make-stamp-online1.com/]http://www.make-stamp-online1.com/[/url] .
Online stamp maker for quick and easy custom stamp solutions
free online stamp maker [url=http://www.make-stamp-online-1.com]http://www.make-stamp-online-1.com[/url] .
Create reusable stamp templates – edit and repurpose designs anytime
stamp online maker free [url=https://www.make-stamp-online-0.com]https://www.make-stamp-online-0.com[/url] .
Free tool to generate cover letters for multiple applications daily
coverletter generator [url=https://www.aicoverlettergenerator.pw]https://www.aicoverlettergenerator.pw[/url] .
Cover letter generator for job seekers – no experience needed
cover letter converter [url=https://www.createcoverletterfree.press]https://www.createcoverletterfree.press[/url] .
Why affiliate programs are the future of online income – Here’s everything you need to know
partners program [url=http://affiliate-b1.com/]http://affiliate-b1.com/[/url] .
Датчик давления в шинах для трейлеров и прицепов — усиленный сигнал
tpms датчики давления в шинах [url=https://datchik-davleniya-v-shinah.ru/]tpms датчики давления в шинах[/url] .